This summary is not available. Please click here to view the post.
Links
FileShareFreak [mirror] THE source for BitTorrent & P2P Tips, Tricks and Info.
Free File Hosting Websites
December 20, 2007 by sharky
Something that’s becoming more and more popular is the use of ‘File Hosting’ accounts to share files. A file hosting service (webhosting) is an Internet service specifically designed to host static content - typically large files that are not web pages. It’s like having an ‘online’ hard drive that you can share with anyone you want, without having to incur the costs of hard drive space and Internet bandwidth.
But are these services appropriate for hosting illegal files? You bet! DDL ‘warez’ websites are a great resource for accessing the links to the copyrighted contraband. Companies that make this service available don’t have the manpower or resources to check all incoming content. Illegal content would be deleted if they received a complaint, or if the infringing content appeared excruciatingly obvious. And if your files get deleted, just move on to the next company - there’s plenty of ‘em.
Archived by FSFmirror
![]()
Categories: DDL / RapidShare
Anonymous BitTorrent
December 18, 2007 by sharky
(BitTorrent over I2P / BitTorrent over Tor / anoNet)
Using BitTorrent to download files is quite possibly the best method going - both for speed and for sheer content availability. And when used alone, it is also the most vulnerable. All P2P users share each others’ information in order to complete a download - thus opening the door to anyone who wants to acquire that info. This is simply a requisite of the deal, quid pro quo. And BitTorrent is no exception to the rule: IP harvesting (of the shared *.torrent file) is especially easy to do with a modified Bit client.
Solutions:
As mentioned here, using a proxy server is a great way to ensure anonymity over any P2P application, including BitTorrent. But there is an alternative - ‘BitTorrent over I2P’.

Archived by FSFmirror
![]()
Categories: Anonymous P2P, BitTorrent
Darknets (Private Internet & File Sharing)
December 16, 2007 by sharky
(Freenet / WASTE / Onionland / I2P / anoNet Darknets)
Well, if you’ve come this far, you can see that we’re treading into some pretty deep water when it comes to Internet security and P2P file sharing - perhaps even considered borderline paranoia. As the saying goes, “You’re not paranoid if they really are out to get you”. For many zealots, this is the only way files should be shared.
Archived by FSFmirror
![]()
Categories: Anonymous P2P
Anonymous Web Searching (& Decentralized Search Engines)
December 15, 2007 by sharky
Faroo
ixquick
Majestic-12
YaCy
Most existing search engines use a ‘centralized’ style of architecture combined with ranking algorithms to generate the ranking of documents crawled in their databases. The best example of this would be the Google PageRank system. However well they perform at generic web page queries, popular search engines are not conducive to finding illegal content on the Internet.
Search engines also log your ’search queries’ including the keywords, IP address and other data of the search, even if you didn’t provide any information. This info is kept in their databases, and there’s no telling how long this info is kept, or what is done with it. Giants like Microsoft (MSN) and Yahoo keep their retention policies private, and Google’s is scrupulous at best.
Want to use the Google Search anonymously? Try Scroogle! They offer free anonymous Google searching through their site. Check it out here.
Archived by FSFmirror
![]()
Categories: Anonymous P2P
Internet Tunneling & Traffic Routing
December 14, 2007 by sharky
(Anonymous Protocols & Networks / Tor / I2P)
IP Tunneling and IP encapsulation (encryption) ensure the reliable delivery of massive volumes of real-time data without packet loss or damage.
Here are three key features in which tunneling becomes beneficial to the P2P file sharer:
- 1.It makes the user anonymous: By masking the real IP address of the user.
- 2.It encrypts the data on both ends: Thus no-one can intercept the transfer and figure out what’s being sent. Helpful in preventing traffic shaping by ISPs.
- 3.It can help circumvent firewalls that would otherwise be implemented to prohibit specific programs and transfers.
Archived by FSFmirror
![]()
Categories: Anonymous P2P
IRCKlipper - The Death of a Giant
December 14, 2007 by sharky
From Sharky: Filesharefreak.com siteop
Not only do sites like TPB, Mininova, Isohunt et al. have the MPAA, RIAA and government agencies breathing down their necks, they’re trying to stay afloat as well. Imagine these ironic headlines:
“Mininova shuts (itself) down: Operating costs too high. MPAA rejoices!”
“ThePirateBay closes: can’t afford the burden of tracking servers any longer.”
OK, maybe this is a little extreme, but it could happen, and does. This is exactly what happened to IRCKlipper.
Archived by FSFmirror
![]()
Categories: IRC, News and Others
P2P Programs Designed for Anonymity
December 14, 2007 by sharky
(P2P Clients & Networks designed for anonymous connectivity)
Alliance P2P
ANts P2P
CSpace
Emscher P2P
Filetopia
GNUnet
i2Phex
iMule
Kommute
MLDonkey
MUTE
MFC-Mute
Nodezilla
RetroShare
Rodi
StealthNet
Other Projects
P2P file sharing is generating a lot of heat these days as countries introduce new copyright laws, stiffer sentencing for Internet pirates, and ISPs that restrict bandwidth for P2P file sharing programs. Fortunately for us, this new-age anti-P2P movement has inspired software developers everywhere to come up with their own counter-measures: Anonymous/pseudonymous P2P applications, encrypted traffic and safeguarded networks. Internet piracy is not exactly going to wither away and die, but it must evolve and adapt to strange days in order to continue to thrive. We’ve learned a great deal from Napster’s peccadilloes and KaZaA’s decoy-prone freestyle nature.
This is the future of P2P file sharing.
Filesharefreak is committed to providing information about these cutting-edge technologies and applications. Listed in this section are some newer (and some not-so-new) methods that incorporate anonymity into your Internet usage and file sharing. This is beneficial in two ways: First, you are out of the prying eyes of anybody snooping on your traffic (like the MPAA and RIAA); second, some client programs/networks support encrypted traffic/routing so that even your ISP can’t tell what you’re downloading (and throttle your bandwidth).
Categories of software include: F2F (Friend-to-Friend), P2P File Sharing, Instant Messaging, Chat, P2P Clients and Networks.
Archived by FSFmirror
![]()
Categories: Anonymous P2P, Other File Sharing Methods
Finding Free eBooks & Audiobooks
December 12, 2007 by sharky
Here’s a list of some common methods for finding eBooks and audiobooks on various P2P networks and protocols.
An eBook, or Electronic book (sometimes spelled “E-Book”), is simply a book, magazine, manual etc. that has been released to digital format. They take many forms, such as *.PDF (Adobe Acrobat) files, *.CHM (similar to a Windows ‘help’ file), *.LIT files (Microsoft Reader) or just plain text files (ASCII). Usually when a book or magazine is converted to these formats (except ASCII), it is professionally done in deliberate support of the program that is opening it, making the reading experience far more enjoyable that reading it in a text editor like Notepad.
An audiobook is a book that has been professionally narrated and saved to digital format. Retail audiobooks are normally found in the form of CD media to be enjoyed in any compact disk player. However, a ripped audiobook will most likely be found as *.MP3 files in order to save space, and can be ‘burned’ to CD media if desired (be advised that many audiobooks will require many CD disks to complete just one book - sometimes as many as 30 - as in the case of unabridged versions). But if you choose this route, use CD-RW (re-writeable) disks so you can use them again afterwards. Many tech-savvy people opt to play these MP3s on portable media players like iPODs, MP3 players and even cell phones.
Archived by FSFmirror
![]()
Categories: News and Others
Using Serials, Cracks & Keygens
December 12, 2007 by sharky
OK, so you’ve downloaded some great software, and you can’t figure out how to get it to work. In general there are only three methods that all ‘Release Groups’ adhere to for getting that illicit piece of software or game to good use: Serial numbers, cracks and key generators.
In a proper release, there is always an information file that accompanies the release (an *.NFO file). It is here that information can be found about how to get the software working normally.
Archived by FSFmirror
![]()
Categories: P2P Tips and Tricks
Bad P2P Programs - What To Avoid
December 09, 2007 by sharky
Some contain crazy spyware; some you just can’t connect to anymore; and some just want your money. Either way, steer clear.
— Adware/spyware-laden P2P clients
— Pay-to-use P2P services/programs
— The iPod $ Music Scam
— P2P programs that don’t connect
— Other things to avoid
Below is a list of some outstandingly BAD P2P clients, as tested in Dec. 2007 - each with a summary. They could have fit into ALL of the categories above.
Archived by FSFmirror
![]()
Categories: Bad P2P
Anonymity Software (Anonymous Proxies)
December 07, 2007 by sharky
Using Software to maintain Anonymity / Anonymous Browsers
Anon Proxy
GoTrusted
JAP
Psiphon
Torpark
SSL Explorer
xB Browser
To compliment web proxies and proxy servers, a software-based approach can help automate the anonymity process. The trick is performed by setting up a SOCKS server (proxy server) that performs the bypass procedure. Not only will most programs allow you to surf the web anonymously, there’s a variety of implications that go beyond the realm of just hiding the IP address. Other useful features include:
- — Using P2P programs from behind a corporate or university firewall.
- — Sending email to recipients via programs that would otherwise be restricted.
- — Using “Messaging” software on prohibited machines.
- — Block popups, ads and spyware.
- — Remove scripts (java) and potentially dangerous activex components.
- — Encryption features, file shredding, cache emptying.
- — Erase your online tracks, history, cookies, temp files.
- — Anonymous web searching
Archived by FSFmirror
![]()
Categories: Anonymous P2P
Anonymous Proxy Servers
December 06, 2007 by sharky
Using ‘Proxy Servers’ to maintain Anonymity
As opposed to web-based anonymous proxies, “real” proxy servers don’t rely on you having to visit their website every time to enter an Internet address, or URL. While generally they offer the same anonymous services as their web-based cousins, proxy servers are embedded into the Internet browser, within the settings. Another key feature is that they can also be incorporated into almost every single application that requires access to the Internet: Online games, FTP programs, P2P filesharing programs - just to name a few.
Like everything else on the Internet, Proxy Servers come in two flavors: Free and Paid.
Archived by FSFmirror
![]()
Categories: Anonymous P2P
How to Browse Isohunt & Torrentspy in the U.S.
December 05, 2007 by sharky
Yeah, we all know Isohunt and Torrentspy have banned access to Americans. If you visit their sites, you’ll probably see something similar to this image (unless, of course, you live in the rest of the world!):
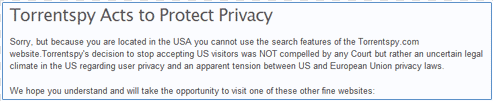
How to circumvent this:
These two websites have blocked U.S. access to their torrents, but this doesn’t mean the exact same torrents don’t exist somewhere else. And the files are hosted by trackers that don’t block American users - the trackers themselves haven’t changed anything (they’re still serving up the same ol’ files to American downloaders from other BitTorrent sites).
All you have to do to start surfing again on Isohunt or Torrentspy, is use an anonymous web proxy (heck, they’re free all over the place) or use a proxy server. There’s even proxy software that’ll allow you “anonymous” web surfing (which is the same thing).
Archived by FSFmirror
![]()
Categories: News and Others
Anonymous Web Proxies & Proxy Servers
December 05, 2007 by sharky
An anonymous web proxy allows anyone to surf the web anonymously (almost) through the web browser. It works by hiding the user’s IP address and any other identifiable information from the websites that they are visiting. This is great for protecting your online identity, or browsing websites that may be otherwise blocked from your location (work, school, library etc.). Privacy is the key benefit to using an anonymous web proxy. They prevent other websites from tracking your browsing habits while protecting your browser history at the same time. Also, they work from any computer, without downloading any software.
Archived by FSFmirror
![]()
Categories: Anonymous P2P
IP Blocking & Blocklists
December 04, 2007 by sharky
Using ‘IP Blocking’ and Blocklists (P2P)
IP blocking/blocklisting is simply a technique used to restrict (block) traffic from any computer that is within a set list or parameters of any given IP range.
While IP Blocking hardly makes oneself anonymous, it can significantly reduce your chances of being tracked by bad groups interested in what you’re doing with your bandwidth. And by no means do blocklists offer 100% effectiveness for file sharing protection. However, when used in conjunction with a proxy server, it can reduce your odds of being caught down to nearly zero.
Archived by FSFmirror
![]()
Categories: Anonymous P2P
Anonymous P2P & Web Solutions
December 03, 2007 by sharky
Keeping safe while sharing files, whether it be while downloading or uploading, is crucial to avoiding any undue attention. When using file sharing programs, computers are susceptible to IP harvesting (collecting) by anyone else sharing the same files - whether it be a *.torrent, or files being swapped on P2P programs such as Limewire.
There are a variety of ways to implement anonymity:
- IP Blocking - blocks snooping IP addresses.
- Web proxies - for anonymous browsing.
- Proxy Servers - to hide your real IP address (web & P2P programs).
- Anonymity Software - to automate the proxy process.
And lastly, use anonymous P2P programs that are specifically designed to achieve anonymity.
Archived by FSFmirror
![]()
Categories: Anonymous P2P
Torrent Search Software
December 01, 2007 by sharky
There’s truly not a lot of BitTorrent ’search’ software - heck, the websites that host the torrent files do a pretty darn good job of searching for torrents! Plus, there are torrent metasearch sites that show aggregated search results for various combined BitTorrent websites. But here’s a few software solutions that may be able to assist in finding torrents that you may not be able to find on your favorite sites.
Archived by FSFmirror
![]()
Categories: BitTorrent
Looking to get in contact with FileShareFreak, or got a great new P2P / BitTorrent scoop, site or idea that you'd like us to cover?
Drop us a line through our Contact page.
FileShareFreak is dead. So we made this mirror site just for the history of Internet, enjoy. Important note: all information provided "as is". No warranties of anything.
Search
Popular Posts
- Rapscallion - A New Community For Torrent Forum Staff
- TheSwarm - New Gazelle Movie Tracker Creating a Buzz
- Pre Database, Scene Release and Dupecheck Websites
- IMAGiNE and Other P2P Groups Collaborate to Create a P2P Tracker
- 20 New Private Trackers: November 2010 Edition
- SceneXpress is Open For Signups, Now Out of Beta
- ThePirateSociety Is Back on a New Domain, New Server
- Active List of FTP Dump Sites For Warez And Music
- The 25 Best DDL Search Engines For RapidShare Links
- IRC Searching on the Web - XDCC Search Sites
FSF Recommends
Categories
- Advanced Searching (10)
- Anonymous P2P (22)
- Bad P2P (18)
- BitTorrent (50)
- BitTorrent Tips and Tricks (27)
- Create your own BitTorrent site (11)
- DDL / RapidShare (17)
- Direct Connect (1)
- eMule / eDonkey (3)
- Gazelle (4)
- Hotline (1)
- IRC (13)
- News and Others (85)
- Other File Sharing Methods (17)
- P2P File Sharing (26)
- P2P Tips and Tricks (26)
- Private BitTorrent (47)
- Private Trackers (96)
- RapidShare / DDL Sites (8)
- Seedbox (38)
- Specialized Private BitTorrent Sites (1)
- Tracker Invites (52)
- Tracker News (30)
- Tutorials and How-To's (17)
- Usenet / Newsgroups (2)
Blog Archive
-
▼
2007
(50)
-
▼
December
(18)
- Torrent MetaSearch Websites
- Free File Hosting Websites
- Anonymous BitTorrent
- Darknets (Private Internet & File Sharing)
- Anonymous Web Searching (& Decentralized Search En...
- Internet Tunneling & Traffic Routing
- IRCKlipper - The Death of a Giant
- P2P Programs Designed for Anonymity
- Finding Free eBooks & Audiobooks
- Using Serials, Cracks & Keygens
- Bad P2P Programs - What To Avoid
- Anonymity Software (Anonymous Proxies)
- Anonymous Proxy Servers
- How to Browse Isohunt & Torrentspy in the U.S.
- Anonymous Web Proxies & Proxy Servers
- IP Blocking & Blocklists
- Anonymous P2P & Web Solutions
- Torrent Search Software
-
▼
December
(18)
FileShareFreak © 2007-2010 / Archived by FSFmirror